If you receive a message from a friend online, how can you tell that it hasn't been altered by cybercriminals before getting to you? How can you ensure the security of your messages and files?
This is where message digests come in. With message digests, you can verify the integrity of media sent over a network. What is a message digest, and how does it work?
What Is a Message Digest?
A message digest is a numeric representation of a message computed by a cryptographic hash algorithm or a function. Regardless of the size of the message, the message digest produces a numeric representation of a fixed size when hashed. It is used to ensure and verify that a message is genuine.
This means that if Bob sends a message or file to you online, you can verify that it has not been tampered with or modified. So when Bob sends the message, he also sends along the message digest he computed. When you receive the message, you then hash it and compare the two message digests.
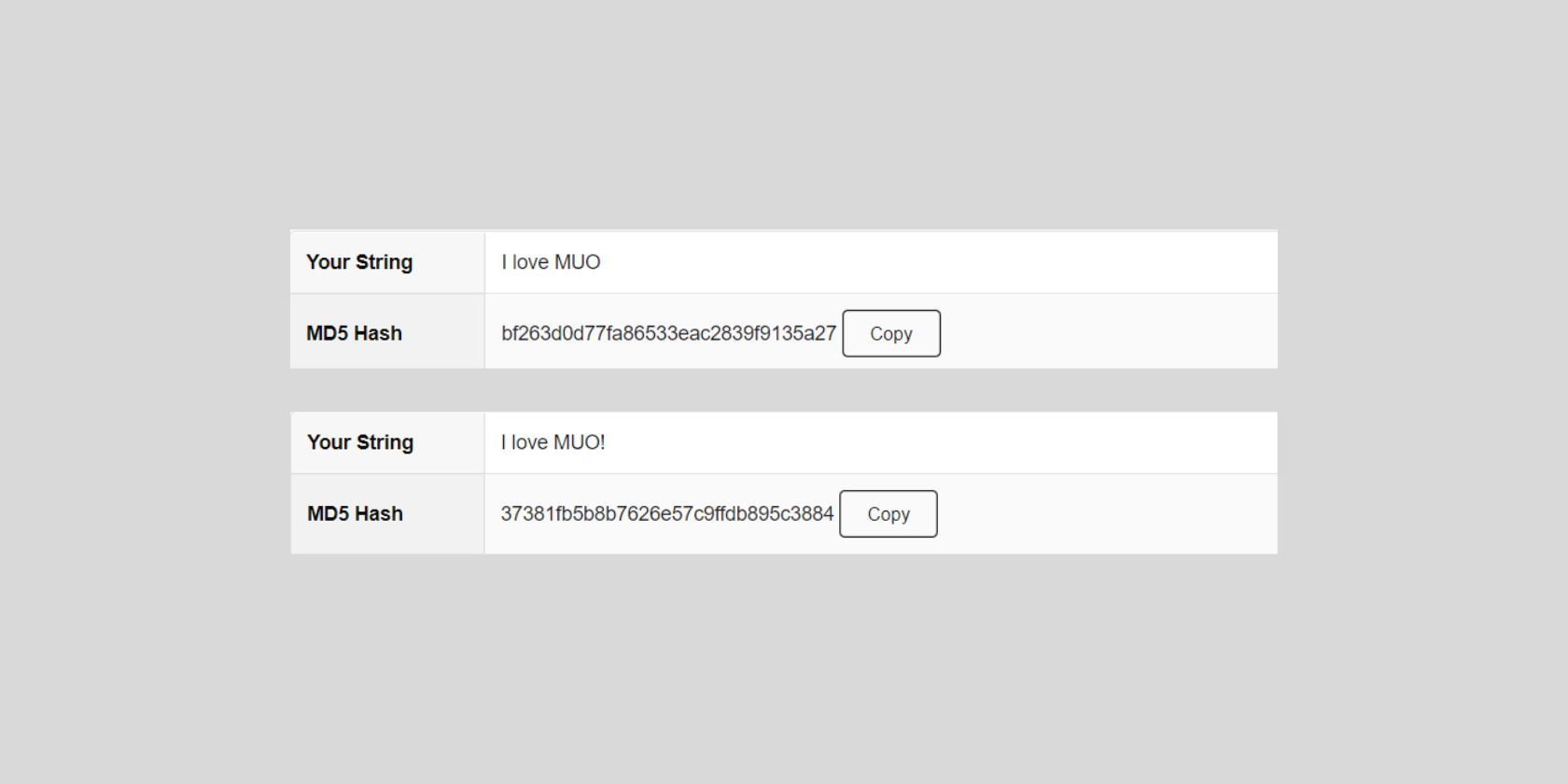
For example, the message "I love MUO" produces a specific hash. If the message is modified just a little by adding an exclamation mark, making it "I love MUO!", the message digest will also be changed. This way, you can verify whether your message has been altered before getting to you.
What Are the Properties of a Message Digest?
What do message digests look like?
- A message digest has a fixed numeric size. If you count the number of characters in the hashes provided in the image above, you see that they both have 32 characters. Each hash algorithm produces a hash of a fixed numeric size. MD5 hashes have 32 characters, while SHA1 hashes have 40 characters.
- It is impossible for two messages to have the same message digest.
- The message digest hashing algorithm is a one-way cryptographic function. This means that it cannot be reversed and it is almost impossible to get the original message from the hash.
Before understanding how message digests work, it is important to understand what a message and a message algorithm are.
A message is any form of media being sent over a network. It is not restricted to text. It could be images, videos, audio, PDF files, etc. A message algorithm is also known as a hash function; it provides a numeric identifier of the message when hashed. Note that the hash function is not the same as encryption, as the hash is irreversible, unlike encryption.
How Does a Message Digest Work?
To use a message digest to verify a message, it has to be sent along with the message itself. When your friend, Bob, sends you a message, he also sends the message digest of his initial message. When you receive it, you hash the received message using the hashing algorithm and get the message digest.
You then compare the message digest Bob sent you to the one you generated. If they are the same, it means that your message hasn't been altered between it being sent and it getting to you.
It is also possible for the person sending you a message to encrypt the digest before sending it to you. This is called a digital signature, and it is an extra layer of security on your communications or transactions. To access the message digest, you need to decrypt it using a public or private key. Only then would you be able to compare it with your generated digests.
What Are Message Digests Used For?
Message digests are used to protect, verify, and ensure the integrity of a message. They are designed to identify and discover changes made to the message. They are used in different fields to protect copyrights and prove ownership.
Message Digests and Integrity Protection
Using message digests is one of the ways to protect and verify how genuine any media is, and whether it's been affected by a third party. With the alarming rate of reproduction and modification of unauthorized works, owners have had to find new ways to protect their copyrights. Another popular method of protecting integrity is the use of digital watermarks.