
Image: Natee Meepian/Shutterstock
Cybercriminals are always changing their tactics in order to achieve their goals. With phishing, the goal is to collect banking credentials, credit card numbers or get access to emails from users, which in turn allows them to run more sophisticated scams, like the infamous business email compromise scam that has affected so many companies for some years already.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
Now some phishing includes advanced social engineering. Abusing LinkedIn is one of those techniques that is very effective because a lot of professionals use and depend on LinkedIn for their activities or work relationships.
LinkedIn phishing emails
In a recent blog post, Kaspersky exposed some examples of this kind of phishing email.
The first one consists of an email supposedly coming from LinkedIn, but actually it has been forged and comes from a real cybercriminal (Figure A).
Figure A
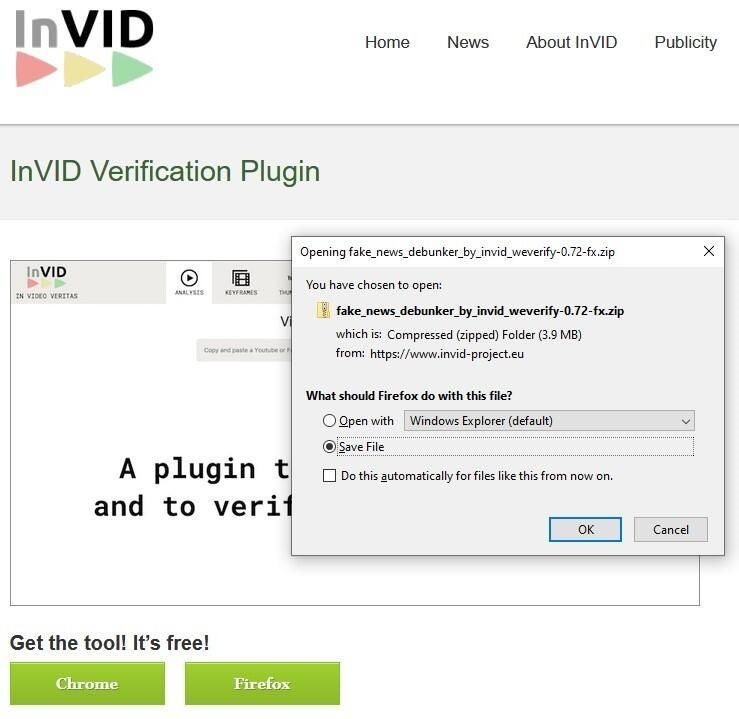
Image: Kaspersky
The content is pretty well done, but what should raise suspicion and detect that this email content is fake is the sender address, which has nothing to do with LinkedIn. Legitimate emails from the social network always use the domain linkedin.com. Also, one might expect such an email not to contain misspellings like “bussinessman.”
Once clicked, the link leads the unsuspecting user to a phishing page hosted on a very different URL than the legitimate one (Figure B).
Figure B
Image: Kaspersky
Once the user enters his or her credentials into this page, the game is over: The cybercriminals will be able to use the user’s account at will.
Kaspersky also warns about phishing emails abusing LinkedIn (Figure C) which leads to a completely different content.
Figure C
Image: Kaspersky
Once again, Figure C shows content that should immediately raise suspicion: the sender address has nothing to do with LinkedIn, and the link to click is also unrelated.
But the weirdest thing happens for the user who decides to click on the link. He or she is not guided to a fake login page supposedly from LinkedIn but to a financial online survey. In that kind of fraud, the user is enticed to fill out a small survey (Figure D) before providing information about themselves, including a phone-number, which might be used to perpetrate other fraud.
Figure D
Image: Kaspersky
Financial crimes from LinkedIn phishing
Most phishing and social engineering attempts that abuse the LinkedIn professional network are done for financial crime purposes.
Some phishing is done to collect direct LinkedIn credentials, or to entice the user to provide other credentials, like personal or corporate email or even phone number or credit card information.
SEE: Google Chrome: Security and UI tips you need to know (TechRepublic Premium)
Once they get hold of credit card information, they can use the card or sell it online. When they get access to the private email address of someone, they can use it for more advanced scams, like impersonating the person to trick some friends into sending money, hunt in the stored emails for more access to other services, or catch private information that can be sold easily, such as passport information.
Owning the access to a corporate account is also juicy for a financially motivated attacker. The attacker might find information to sell or find enough information to build a real BEC fraud.
Fake LinkedIn profiles used for cyber-espionage
In recent years, there have been several examples of real cyber-espionage threat actors abusing LinkedIn to get in touch with employees of companies they want to compromise.
In June 2020 ESET, a Slovak internet security company, exposed “Operation In(ter)caption,” targeted attacks against aerospace and military companies in Europe and the Middle East. In that cyberespionage operation, the threat actor used LinkedIn-based social engineering to establish an initial foothold before deploying malware (Figure E).
Figure E
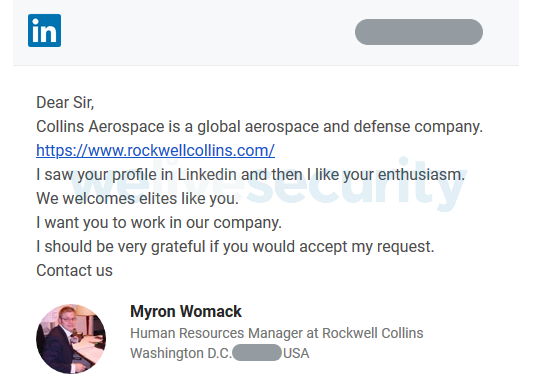
Image: Kaspersky
In this case, the attackers had created a false profile on LinkedIn and used it to approach employees in companies they wanted to target. Once the talk was initiated, they would socially engineer the victims to have malware launched to compromise the company.
In another case, an investigation from the Associated Press revealed the use of an artificial intelligence-generated picture set on a fake LinkedIn profile under the name “Katie Jones,” who targeted several think tanks’ profiles.
How to detect LinkedIn phishing and fake profiles
LinkedIn phishing can be tricky to detect because some phishing emails can look very convincing. So, how can you spot LinkedIn phishing?
- First, look at the sender information. It must come from an email address at linkedin.com. Yet if it does, it does not mean the content is not fake.
- Look for typos and misspellings in the subject line and the email body.
- Look at the link that you need to click to go further. If it brings you to a URL that is not using the linkedin.com domain, it is phishing.
- If it contains an attached file, it is fake. LinkedIn will not send you files. It is probably a file that will infect your computer if opened.
- In all cases, if you suspect something, disregard the email, open your browser and access LinkedIn the way you usually do. You can then see what’s up in the user interface and handle it safely.
Now what about the fake profiles on LinkedIn?
- Check all of the profile. Are there inconsistencies or weird information?
- Check the contacts or the number of contacts. If the number is very low, it might be a newly created profile set up for fraud.
- Does it make sense that this person contacts you?
- Does the person want to share files with you? Maybe even in an urgent manner?
If you have doubts and really are curious about the message, don’t hesitate to call the main office at the company. Ask for the person. For starters, they will confirm the person exists in the company. Then get the person on the phone and confirm it is indeed the person who sent you the message.
Remember that cybercriminals can also compromise LinkedIn accounts and use them. Therefore, it’s important to have confirmation via another communication channel when receiving weird messages on LinkedIn.


