Apple releases emergency updates for iOS, iPadOS, macOS and watchOS 7.6.2 to prevent Pegasus spyware
Apple has released an emergency update for iOS devices and macOS computers, to patch a serious security vulnerability that has come to light. The exploit is called FORCEDENTRY, and affects all iOS devices, Mac computers and Apple Watches that haven't been updated to the latest firmware.
Here's how the security threat was unearthed.
Canadian security research company, Citizen Lab, obtained a phone from an anonymous activist from Saudi Arabia in March 2021. The iPhone was believed to have been infected by Pegasus, a spyware that was developed by NSO Group.
Citizen Lab extracted a backup of the device from iTunes, and began analyzing its contents. The forensic procedure found several .GIF files were present in the phone's iMessage app, and these had been received just before the device had been compromised.
What's interesting here is that these files weren't actually GIFs, some of them were Adobe PSD files and others were PDFs. The malicious files contained some arbitrary code that caused crashes on the phone, allowing it to be hacked. This was how the FORCEDENTRY exploit chain infected the device with the Pegasus surveillance tech. These weren't just zero-day attacks, but also zero-click exploits, meaning they needed no intervention from the user to infect the device. The security exploit targets Apple’s image rendering library, called CoreGraphics, causing an integer overflow.
The security group says the mitigation may have been actively used since February 2021. The FORCEDENTRY exploit was supposedly developed to bypass Apple's security updates that were patched in the BlastDoor security system.
Citizen Lab sent its discoveries to Apple on September 7th, and the Cupertino company after analyzing the samples, confirmed that the files contained a zero-day exploit that impacted iOS and macOS devices.
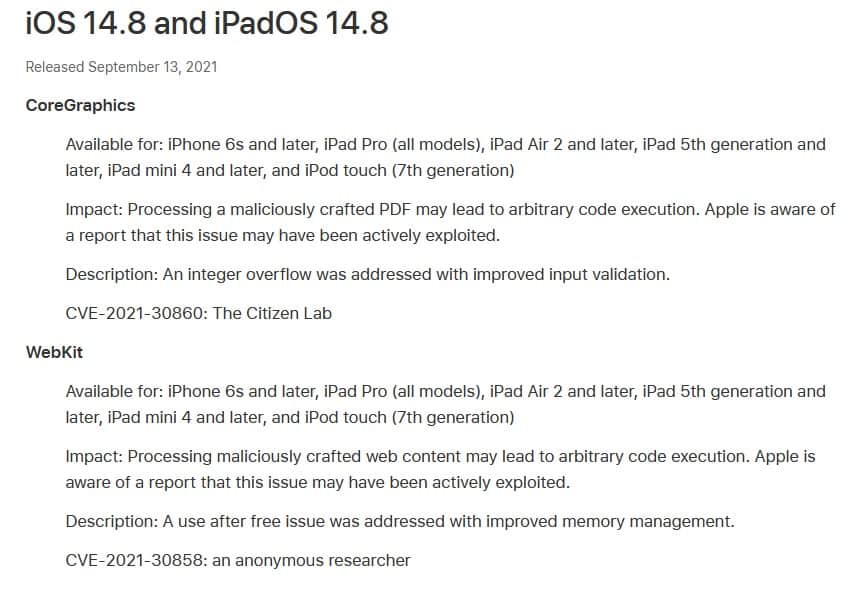
Apple has assigned CVE-2021-30860 for the security issue. Today, the company released a new update for iOS devices and macOS computers to address the vulnerabilities. The updates also ship with an additional zero-day patch (CVE-2021-30858), that prevents arbitrary code execution via malicious web content.
iOS 14.8 and iPadOS 14.8 are available for iPhone 6s and later iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation). Mac systems can be updated to macOS Big Sur 11.6 for the latest security patch. watchOS 7.6.2 has also been released for Apple Watches.
References: Apple 1, 2, and 3.
TechCrunch reports that Apple released a statement that confirmed the rapid development and deployment of iOS 14.8 update. The company also commended Citizen Lab's efforts in discovering the exploit. The statement from Apple indicates that such attacks are sophisticated, costs millions of dollars, and are often used to target specific people, and not the general populace.
Nevertheless, it is good to see that Apple acted quickly to patch the security loophole has been patched, which in turn protects all users. Please refer to Citizen Lab's announcement for technical details regarding the discovery of the FORCEDENTRY exploit.
If you are using an iPhone, iPad, Mac or an Apple Watch, you should update your device immediately to avoid potential security issues.
Wasn’t it only two weeks ago that Apple was getting slammed about their Trojan Horse anti-privacy “policy” of checking for child exploitation?
Now suddenly there is a super-mega-critical emergency update based off a source from Israel?
…and no one has has bothered to comment on any of this to boot?!